Nft Add Rule Nat Postrouting Masquerade
For example, if the ens3 uses the 198.51.100.1 ip address: If the ens3 interface uses a static ip address, add a snat rule.

February 2015 Wannabe Exceptional
% nft add rule nat postrouting masquerade.

Nft add rule nat postrouting masquerade. In reality you for sure will add a more complex set of rules. I needed to add in firewalld 0.9.3 the following direct rules: Nft list ruleset > /etc/nftables.conf 1.2.
Performing network address translation (nat) create a rule to translate the ip address coming from the network 192.168.1.0/24 and count it before sending. Nft add chain ip nat postrouting '{ type nat hook postrouting priority 100; The ip and port that should be used for snat or dnat are passed as args to add_nat ().
Nft add rule nat postrouting ip saddr 192.168.1.0/24 counter masquerade. In routers that would be our wan interface, and for vpn servers our lan interface. Masquerade is available starting with linux kernel 3.18.
Add a table and postrouting rules to perform network address translation (nat) on packets that have passed through the server: We will need to add a nat rule that masquerades all outgoing traffic to a specific interface. No such file or directory when adding chain
I have added the whole file as a reference below , so you can see the positioning of the lines. Masquerade is a special case of snat, where the source address is automagically set to the address of the output interface. I am able to add the nat table, and also the postrouting chain, to the nft configuration.
For the first rule i used insert instead of add, so that it is inserted as first rule of the postrouting chain, thus before the masquerade rule. }' the rule would be: #set masquerading directive ${nft} add rule nat postrouting masquerade if you piece all these snippets together, it should give you a functioning nftables router/firewall.
For example, run the following command in the shell terminal: However i cannot get anything like the following command to work: I have a linux box which i use as a router for other pc on different vlan.
In all cases i've tried, i get the following: # nft add rule nat postrouting oifname ens3 snat to 198.51.100.1 additional resources for more information, see section 6.3.1, “the different nat types: Now enable packet forwarding in the linux kernel.
Config_nf_tables_ipv4 and that the module can be loaded (eg. Nft create table ip nat nft create chain ip nat postrouting {type nat hook postrouting priority srcnat\;} nft add rule ip nat postrouting oif eth1 masquerade nft create table ip filter nft create chain ip filter input {type filter hook input priority filter\;} nft create chain ip filter forward {type filter hook forward priority filter\;} nft. If you have a static ip, it would be slightly faster to use source nat (snat) instead of masquerade.
A rule that enables nat so that packages can be routed back to the vpn painlessly. Setup_rule () calls add_nat () where expression for snat is built. Nft insert rule nat postrouting oif eth1 ip daddr 192.168.2.0 / 24 accept nft add rule filter forward iif eth1 oif eth0 ip saddr 192.168.2.0 / 24 ct state new accept.
Masquerading, source nat, destination nat, and redirect” Nft add chain nat postrouting { type nat hook postrouting priority 100 \; Please, see how to configure tables.
The following is an example of nftables rules for setting up basic network address translation (nat) using masquerade. Ip daddr 192.168.22.5 udp dport 53 counter masquerade this won't affect any return traffic initiated from the dns server, because its conntrack entry will not be in state new anymore and this nat rule won't be traversed. Nft add rule nat postrouting ip saddr 10.5.6.0/24 oif eth0 masquerade take a look on nftables nat wiki for more informations.
I'm trying to set up nftables to masquerade source addresses on the axc f 2152. } 3 nft add chain nat postrouting { type nat hook postrouting priority 100 \; You can write the rule this way:
} 4 nft add rule nat postrouting ip saddr 10.8.0.0/24 masquerade You have to create the table before you can actually list it, ie. # nft add rule nat postrouting oifname ens3 snat to 198.51.100.1
Note that masquerade only makes sense from postrouting chain of nat type. Moreover, make sure you also compiled family support, eg. } nft add rule nat postrouting ip saddr 10.0.8.0/24 masquerade.
We will do this by creating a new table with a postrouting chain containing a rule which will masquerade the original adress/port pair. If the ens3 interface used dynamic ip addresses, add a masquerading rule: # nat table rules *nat :postrouting accept [0:0] # forward traffic from eth1 through eth0.
This way the router would replace the source with a predefined ip, instead of looking up the outgoing ip for every packet. 1 nft add table nat 2 nft add chain nat prerouting { type nat hook prerouting priority 0 \; Add a nat rule to translate all traffic from the 192.168.0.0/24 subnet to the host's public ip:
Nft add rule nat postrouting masquerade. # nft add rule nat postrouting oifname ens3 masquerade; Iptables masquerade rule can be replaced with snat rule.
Here, main () function calls setup_rule () where whole rule is built. Sudo nft add rule nat postrouting ip saddr 192.168.0.0/24 masquerade show rule handles:
Nft-rulesvpnmd At Master Mqusnft-rules Github
Dual Wan Flow Base Pcc Nftables Load Balancing Example Script Github

February 2015 Wannabe Exceptional
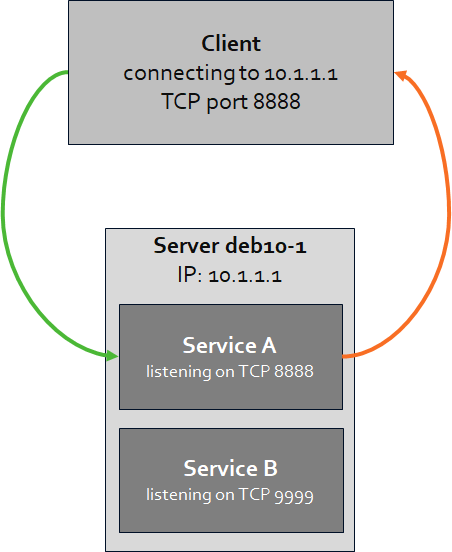
Forward A Tcp Port To Another Ip Or Port Using Nat With Nftables Jensds Io Buffer
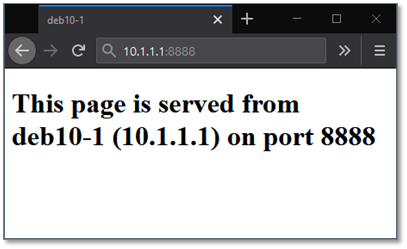
Forward A Tcp Port To Another Ip Or Port Using Nat With Nftables Jensds Io Buffer

Linux Iptables Delete Postrouting Rule Command - Nixcraft

How To Configure Nftables Successor Of Iptables

How To Configure Nftables Successor Of Iptables

Netfilter Framework Providing Hooks System For Nftables

How To Setup Router On Red Hat 8 With Nftables - Youtube
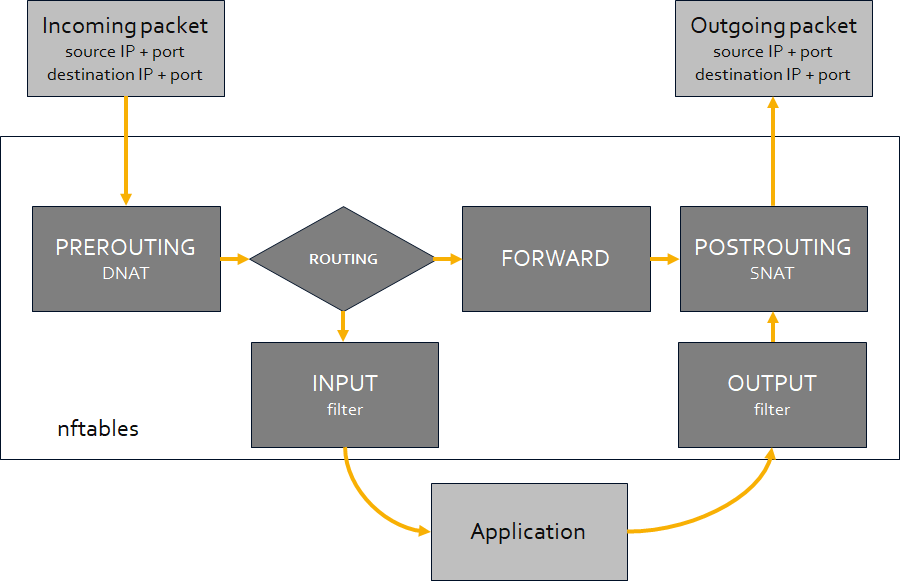
Forward A Tcp Port To Another Ip Or Port Using Nat With Nftables Jensds Io Buffer

Linux How To Clone The Output Of The Masquerade Target With A Tee Itectec
Implement Expression For Matching On Source Ip Issue 5 Googlenftables Github

Forward A Tcp Port To Another Ip Or Port Using Nat With Nftables Jensds Io Buffer

Nftables Configure That Linux Firewall Like An Expert

Membuat Wifi Sendiri Dengan Hostapd Dhcpd Dan Nftables Wannabe Exceptional
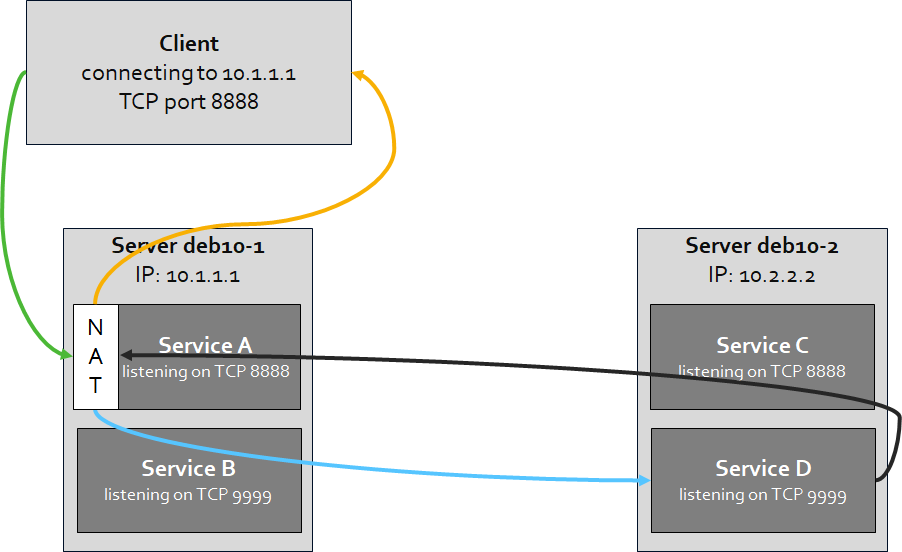
Forward A Tcp Port To Another Ip Or Port Using Nat With Nftables Jensds Io Buffer
Nftables 6 A Nftables Linux Internet Gateway - Computer Outlines Blog

